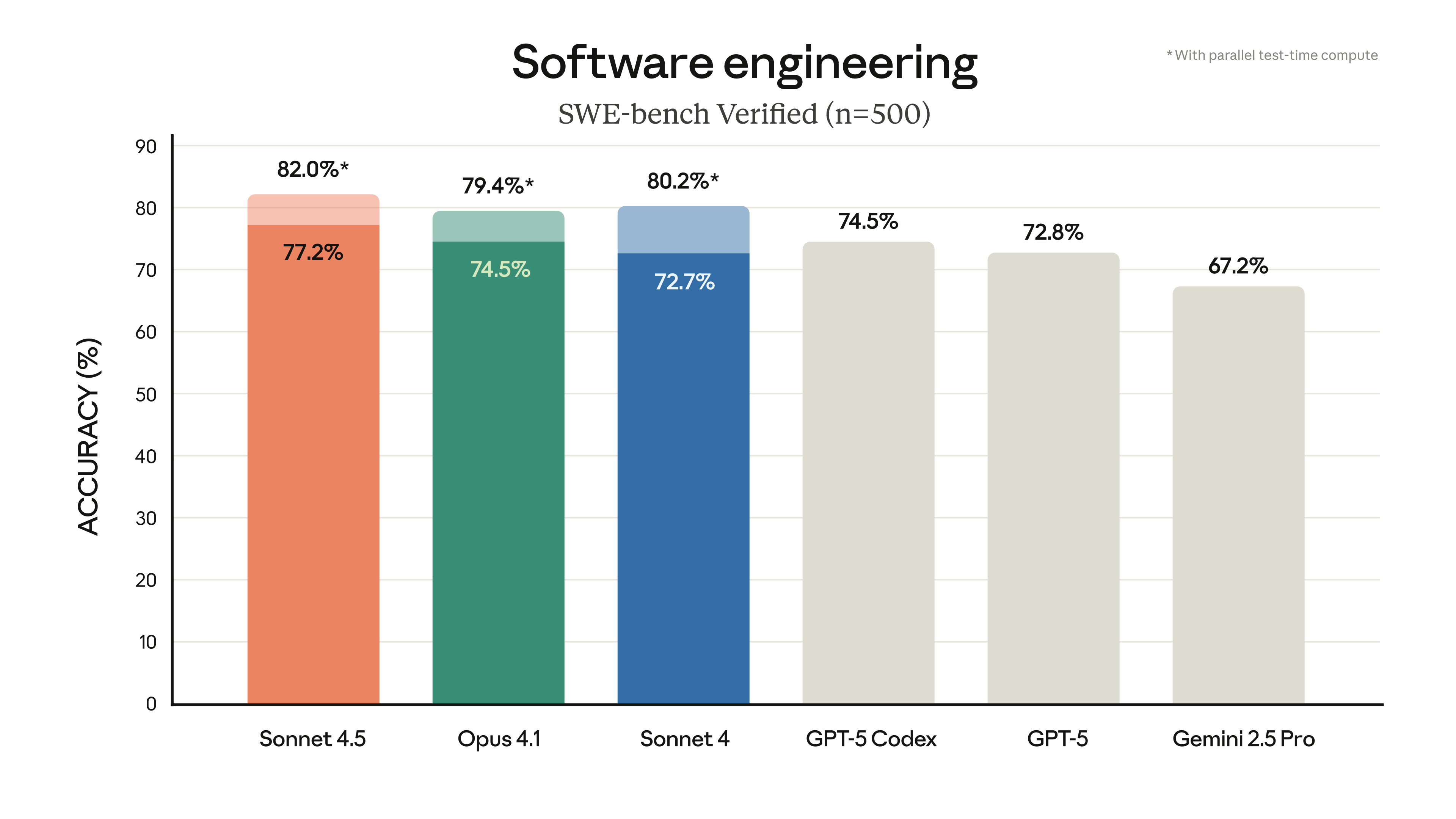
Implementation Steps for Security Protection Architecture
According to the reverse engineering report, Claude Code's 6-layer security protection system can be broken down into the following landable solutions:
- Input validation layer: Use the sanitizer.js template in the scripts/ directory of the repository to perform XSS/SQL injection detection on all user inputs
- Permission validation chain: Realize the "UI→Session→Tools→Parameters→Sandbox→Log" six-fold validation described in the document. Pay special attention to the design of the permission verification module in tools/security/.
- Sandbox segregation program: 1) Containerized execution environment using Docker 2) Memory isolation via WebAssembly 3) Refer to chunks/sandbox.mjs to set resource quotas (CPU/memory/runtime)
- Dynamic monitoring system: Integrate the anomalous behavior detection module mentioned in the project documentation to terminate the process when circular dependencies, abnormal system calls, or resource overruns are detected.
Caveat: The FINAL_VALIDATION_REPORT.md of this project states that the complete implementation of its security architecture needs to be weighed against performance loss (~15-20% latency increase), and it is recommended that the level of protection be selected based on actual needs.
This answer comes from the articleanalysis_claude_code: a library for reverse engineering Claude Code.The