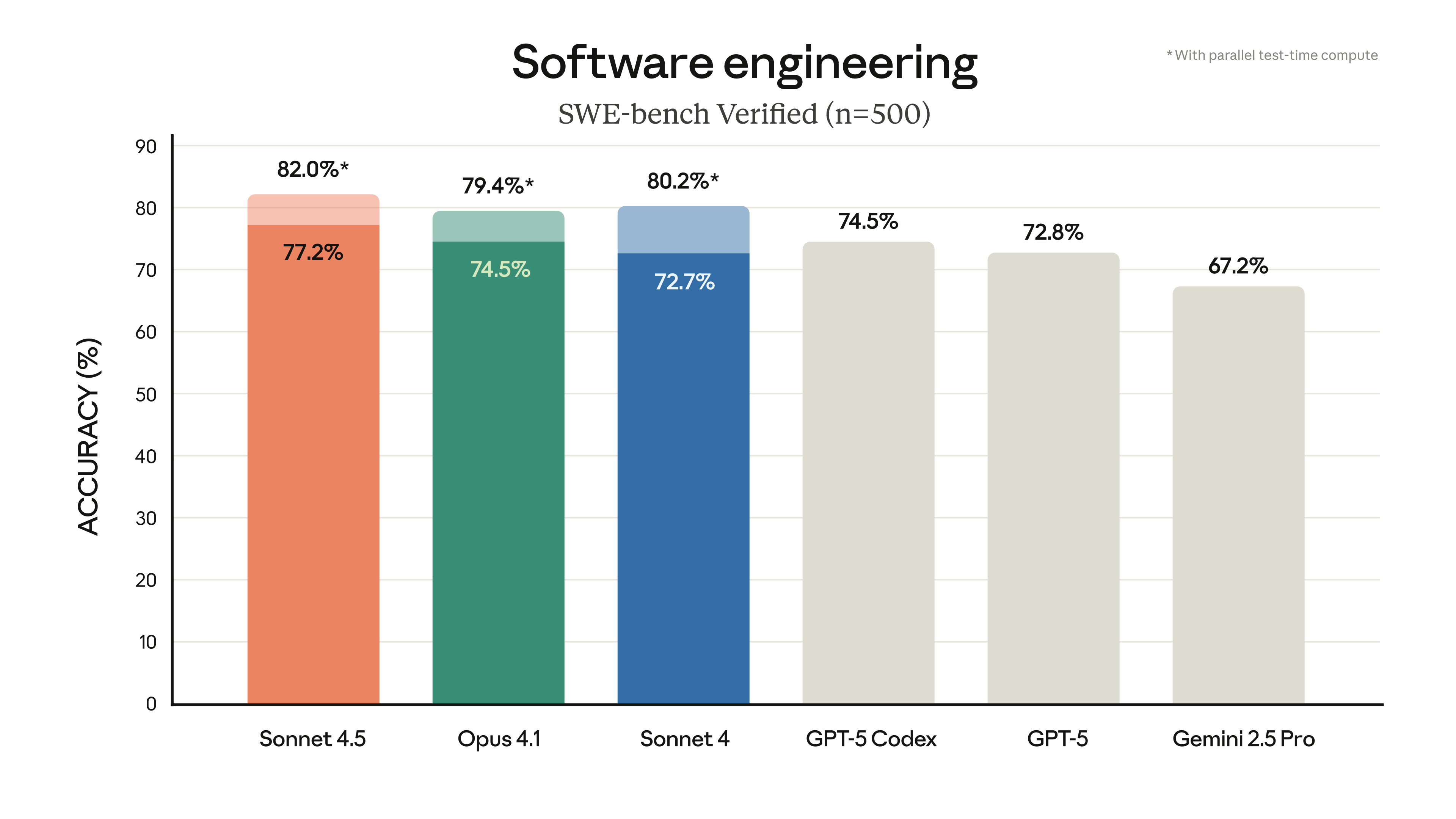
Guidelines for the Implementation of Secure Segregation
The scope of risk impact can be effectively controlled through environmental isolation, which is done in three stages:
- development phase: Forces the use of the tool's own fuzzing output function (which automatically adds the *** suffix), via the
venv/bin/activateLimit the scope of reliance - testing phase: When running a full inspection inside a Docker container, be sure to add the
--network noneDisable network to prevent accidental data transfer - pre-emptive stage: Adoption
docker cpExport test reports and disable direct mounting of host directories
Special note: When integrating with the extendable-agents project, be sure to configure the"dangerous-mcp"for the least privileged role. All test data is recommended to use thefakerThe library generates spurious environment variables.
This answer comes from the articleOpen source tool for detecting security risks in MCP servicesThe