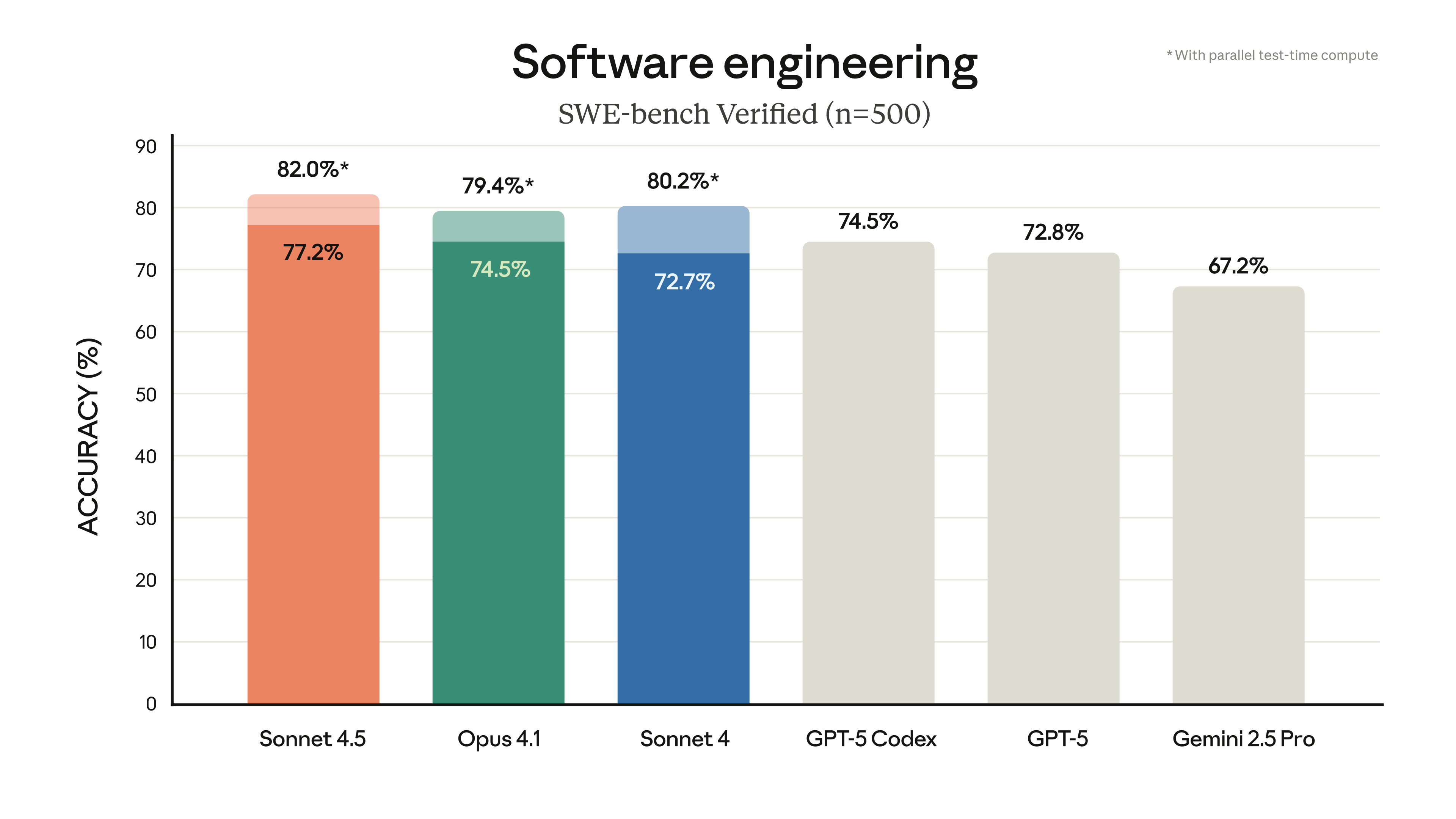
Secure Reconfiguration Protection Mechanism
To ensure the security of automated reconfiguration, a triple protection needs to be put in place:
- test sandbox: Forces Codex to enforce changes before they are submitted:
- Complete test suite (configured in AGENTS.md)
- Customized static checks (e.g. SonarQube rules)
- Code change impact analysis (via coverage comparison)
- Change isolation::
- Require Codex to generate a separate commit for each task
- Prohibit modification of the history of submissions
- Read-only whitelisting of core files
- verification process: should be examined when reviewing the evidence package provided by Codex:
- Number of failed retries in the test log
- Severity level warning for static analysis tools
- Visualizing git diffs of changed files
For business-critical modules, it is recommended that theShadow TestStrategy: let Codex run a test environment deployment without merging code first and verify that there are no exceptions before approving the merge request.
This answer comes from the articleChatGPT Codex: Intelligence for Automating Software Engineering TasksThe