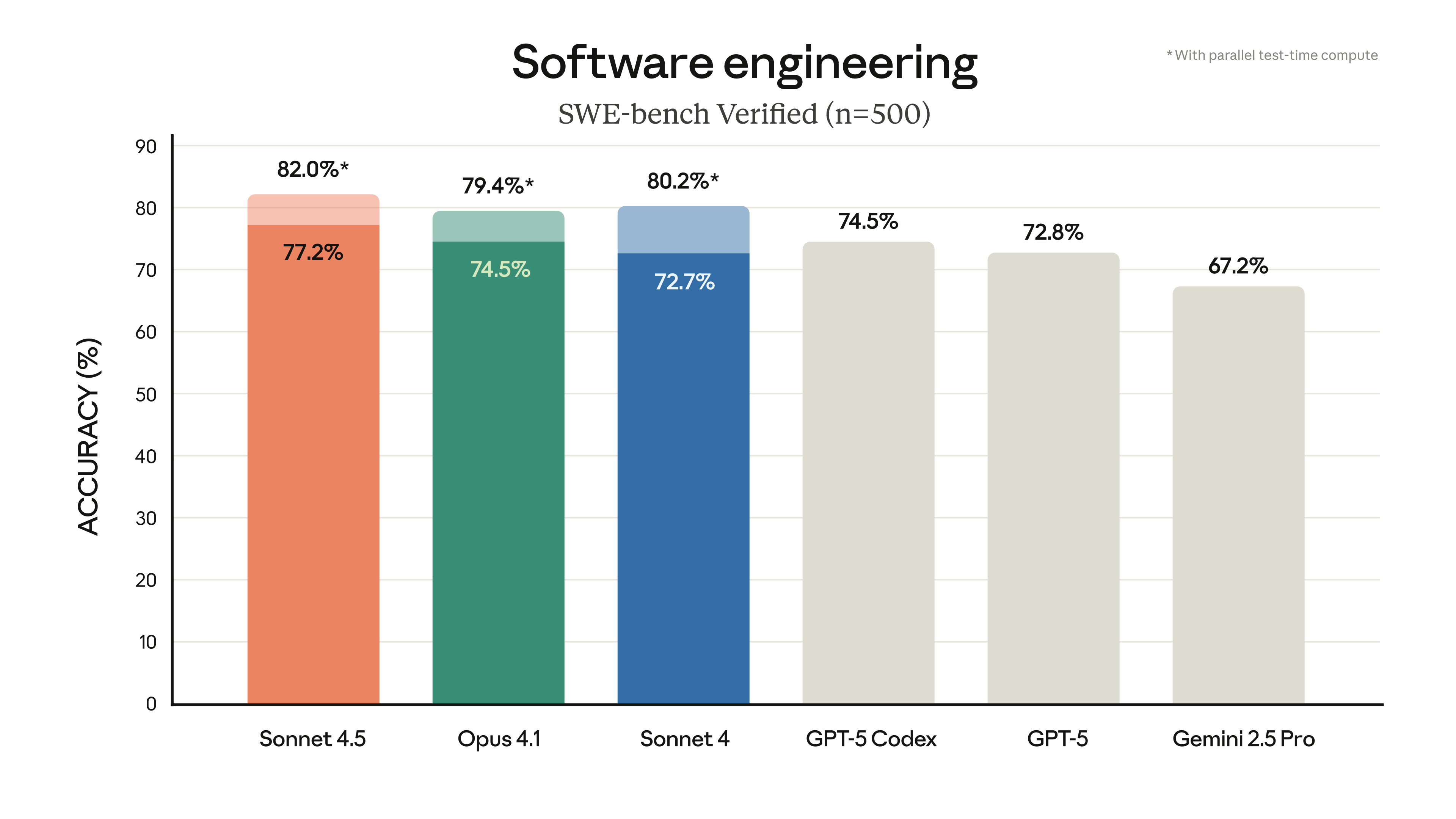
Sources of risk
Keys hard-coded in client code or uploaded to public repositories are the main leakage channels, which may result in overages.
Protection Program
- Environment variable storage::
import os
API_KEY = os.getenv("SERPER_KEY") - server-side proxy: Build a middle-tier API to forward requests without exposing the original key on the front-end
- IP whitelisting: Setting the range of Allowed IPs in the Serper backend (paid feature)
emergency response
- Discover the leak immediately by clicking on the consoleRegenerate Key
- Checking the usage page of theUsage by IPdiagrams
- Enable email alerts (1TP per month for TP4T5 and above packages)
Additional recommendations: Development and production environments use different keys
This answer comes from the articleSerper: the API tool for 2,500 free uses of Google search resultsThe