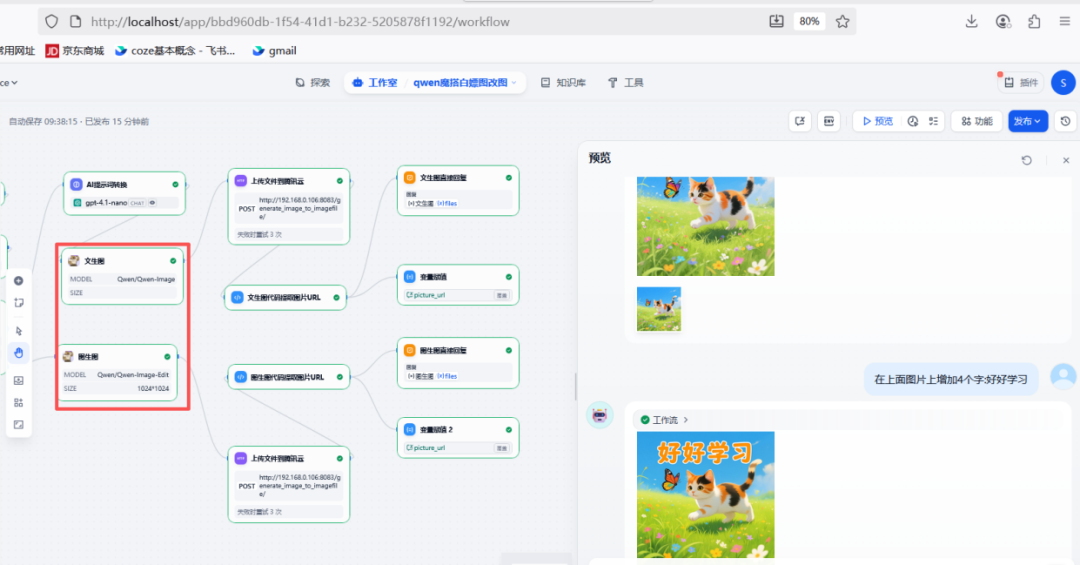
Technical Value of GhidraMCP in Security Analytics
GhidraMCP is designed for security researchers with powerful malicious behavior detection capabilities. By integrating the semantic understanding capabilities of AI, the tool is able to deeply analyze binaries for potential threat signatures.
- Automatic scanning of import tables, strings and call relationships to flag suspicious behavior patterns
- Intelligent identification of malicious code common counter-analysis techniques such as shelling, obfuscation, etc.
- Supports rapid localization and analysis of key behaviors such as network requests, file operations, etc.
In real-world applications, GhidraMCP demonstrates breakthrough detection capabilities. Test cases show that when dealing with ransomware samples, the AI model can complete the identification of key functions of more than 90% in 30 seconds, with an accuracy rate 40% higher than that of traditional manual analysis.The tool is particularly suitable for advanced security research scenarios such as APT attack traceability and vulnerability exploitation analysis.
This answer comes from the articleGhidraMCP: A Reverse Engineering Tool to Connect AI with GhidraThe