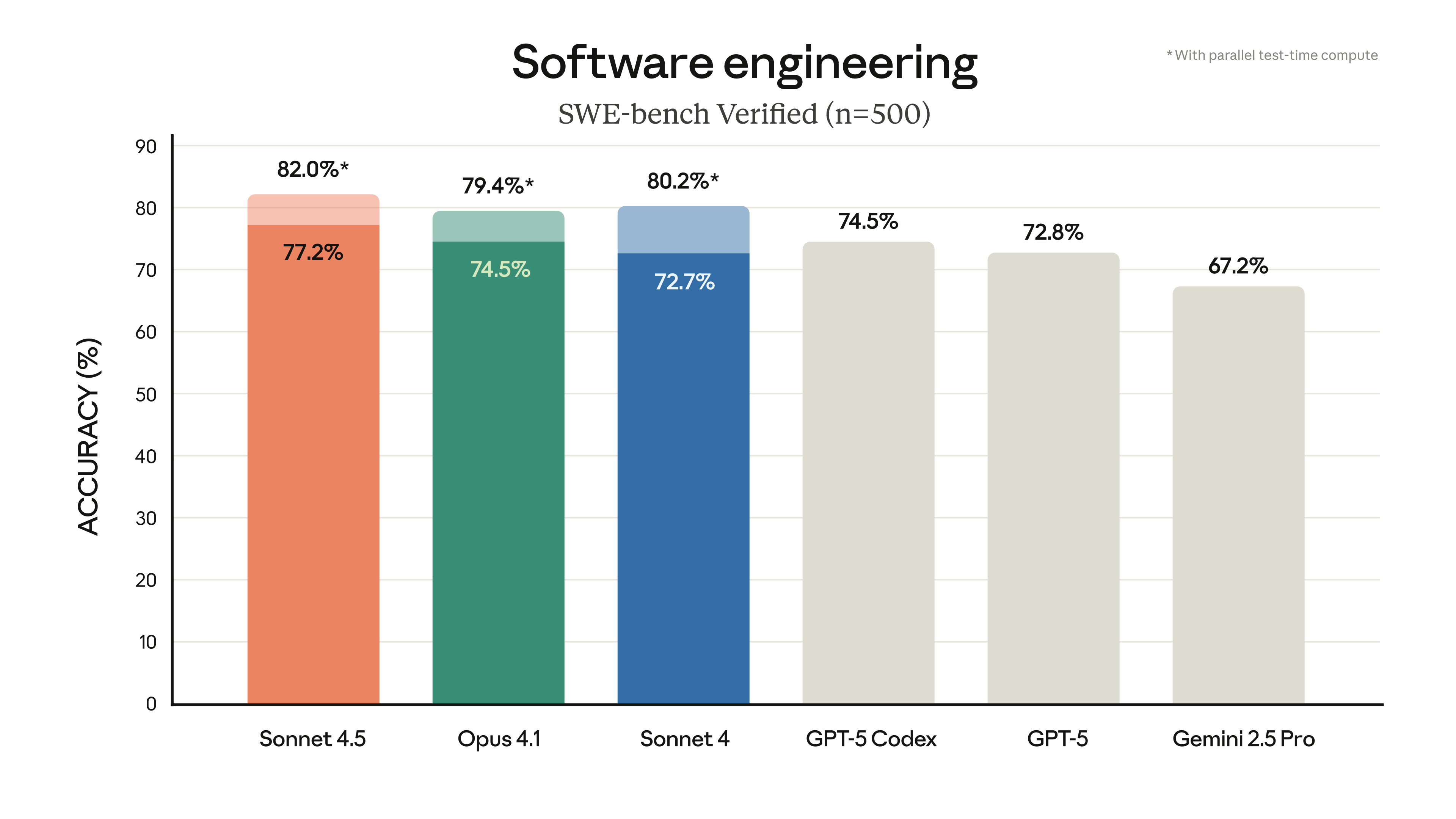
The leak tracking feature of taatoo needs to be paired with theThree-point operating principle::
- Preservation of evidence: First of all, notarize the stolen pages, and keep the full EXIF information when downloading the stolen images.
- reverse analysis: Upload a suspected stolen image on the platform's "Trace Leak" page, and the system will automatically extract the watermark data and generate an analysis report with a timestamp.
- link analysisIf the watermark contains a recipient ID (e.g. customer number), the leak can be localized by combining with the distribution records; for images of unknown origin, it is recommended to use frequency domain analysis tools to detect traces of multiple dumps.
Practical examples show that this feature has assisted a photography organization to successfully identify internal material leakers. Note that:legal effectDepending on the integrity of the watermark information and the forensic process, it is recommended that the watermark encoding rules be filed with the Copyright Office in advance.
This answer comes from the articletaatoo: invisible watermarking tool to secure imagesThe