Codex is designed with military-grade security architecture, and its sandbox environment has triple protection features: network isolation (disabling external connections), storage encryption (AES-256 encrypted temporary storage), and operation auditing (full-link logging). Each task session creates a new independent container and destroys all temporary data immediately after the task ends, ensuring that the code is not persistently stored in the cloud.
Security test data showed that the system successfully resisted simulated penetration of all OWASP Top 10 attack vectors, including: blocking credential theft attempts injected via environment variables, disabling dangerous system calls (e.g., subprocess.popen), and filtering commits containing sensitive keywords (e.g., aws_access_key). A bank reverse-engineered Codex during the PoC phase and confirmed that it was unable to obtain unauthorized code snippets through a side-channel attack.
In terms of access control, Codex follows the strict least privilege principle. It can only clone Git repositories explicitly authorized by the user and has no access to any resources on the host. Audit logs automatically record all commands and file changes executed by the smartbody, and this chain of evidence is submitted with the Pull Request for review by the security team.
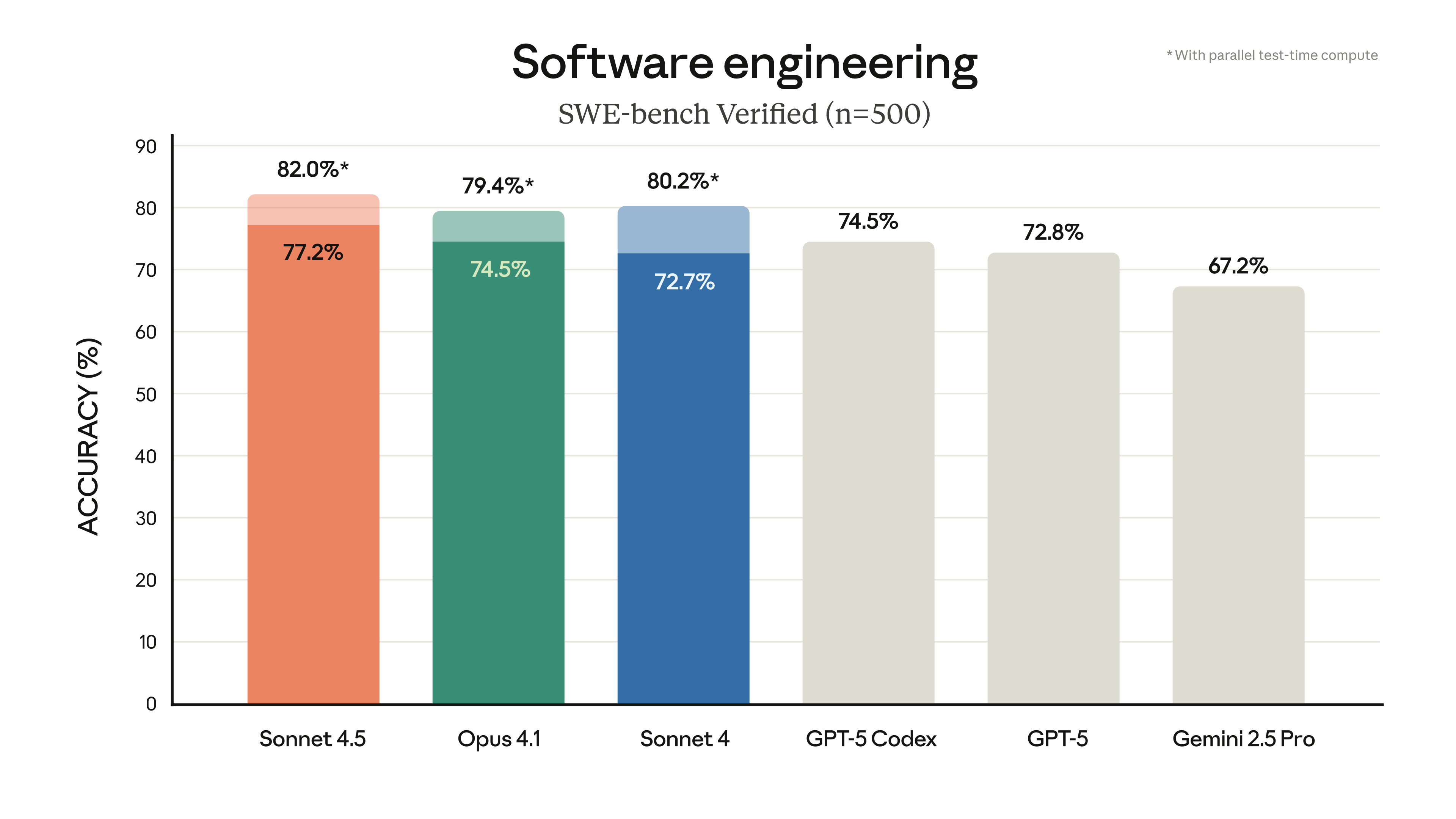
This answer comes from the articleChatGPT Codex: Intelligence for Automating Software Engineering TasksThe