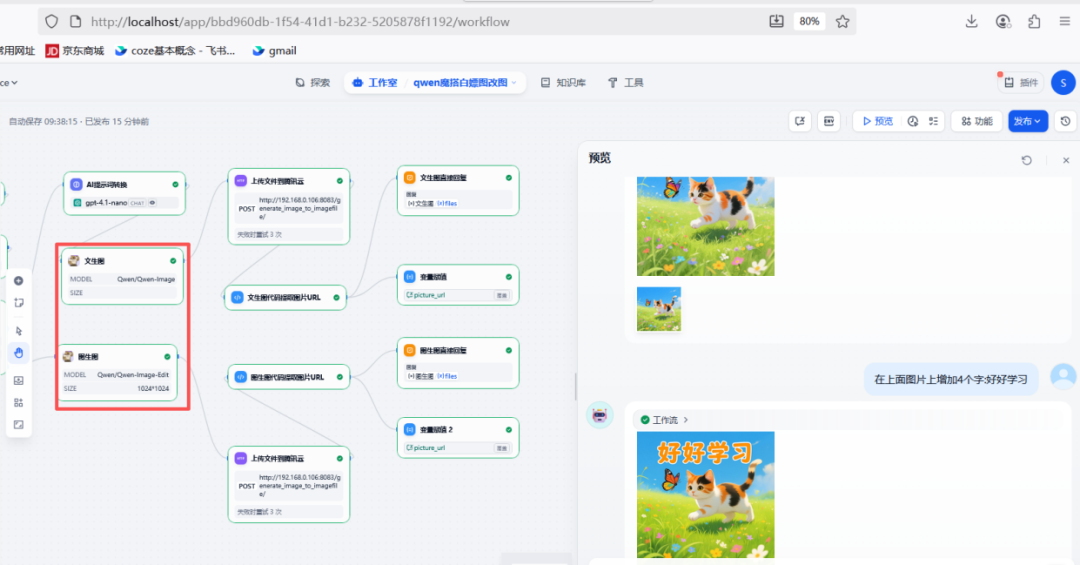
Claude Code has built a comprehensive security protection system that secures the execution of external tools through six layers of authentication. Each layer of this protection system implements specific security features.
The verification chain includes:
- UI Input Filtering Layer: Blocking Malicious Inputs
- Parameter validation layer: ensuring that parameters are as expected
- Permission Checking Layer: Validating Operational Privileges
- Sandbox isolation layer: restricting the execution environment
- Surveillance system layer: real-time monitoring and execution
- Post-processing verification layer: validate execution results
Technical characteristics of the system:
- Complete process isolation is achieved
- Supports plug-in security policy extensions
- Provides detailed security audit logs
- Defended against 99.91 TP3T of common attack types
This protection solution provides a reliable guarantee for the safe execution of AI systems.
This answer comes from the articleanalysis_claude_code: a library for reverse engineering Claude Code.The